Bill Owen, consultant for Invensys Critical Infrastructure & Security Practice, discusses the rules, requirements, and standard methods for preparing for incidents and provides methods for responding to actual events.
All nuclear power plants in the United States are regulated by the Nuclear Regulatory Commission (NRC) and are required to implement certain security controls. Any systems considered Safety, Security, Emergency Preparedness, and/or Support Systems (SSEP) are required by law (NRC 10.CFR.73.54) to have certain controls in place.
Cyber security programs at U.S. nuclear facilities are subject to 10.CFR.73.54, Protection of Digital Computer and Communication Systems and Networks, and must consider following Regulatory Guide (RG) 5.71, Cyber Security Programs for Nuclear Facilities, or an approved alternate method when implementing these programs. Accordingly, the Nuclear Energy Institute (NEI) developed an approved alternative to satisfy the rule, NEI 08-09 Revision 6: Operational, Management, and Security Controls. RG 5.71 and NEI 08-09 were both built on NIST 800-53 standards.
Cyber Security Plans (CSP) for all United States nuclear plants have been developed and the NRC has approved these plans. Section 4.6 of these Cyber Security Plans requires licensees to put in place a comprehensive Incident Response Plan (IRP). These plans are required to include processes to detect, deter, and respond to cyber attacks while mitigating the effects of the attacks and documenting forensic information (records) pertaining to the attacks if kept.
A cyber incident response capability must include several elements that are proactive in nature to prevent an incident or better allow the organization to respond when one occurs. These elements are green in Figure 1 and include planning, incident prevention, and post-incident analysis/forensics. Other elements center on detecting and managing an incident once it occurs. These are reactive in nature and are typically carried out under severe time constraints and great visibility. These elements, shown in red in Figure 1, include detection, containment, remediation, recovery, and restoration.
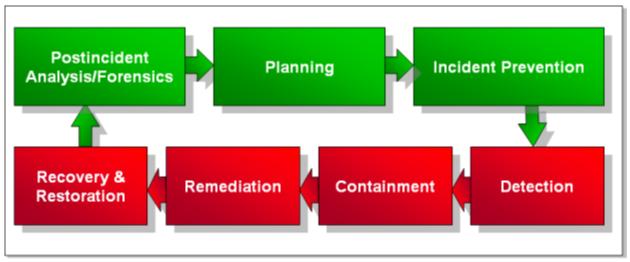
The figure above is from an excerpt of the Homeland Security October 2009 Recommended Practice, Developing an Industrial Control Systems Cyber Security Incident Response Capability document. Future articles will go more into detail in each of the areas identified above and provide details on how CISP can support the effort to put comprehensive Incident Response Plans in place and maintain them during the lifecycle of the Cyber Security Programs.
Want to win a Dell Tablet? Read the rules below and take the survey for this post here.
**Remember, if you take the survey, please leave a comment with your name and let us know you took it!**
Dell Tablet Giveaway
We want to hear from you, so we're giving away a Dell tablet! Keep up to date with the Invensys cyber security team through a pre-loaded Android app and have easy access to The Cyber Advisor Newsletters as well as datasheets and service profiles about our solutions.
During the month of May, there will be 2 blog entries a week that contain a link to a survey related to that post. The rules are simple. To qualify, you must take the survey and leave a comment saying you completed the survey. The more blogs you read, the more surveys you take, the greater your chances of winning. The winner will be announced on the blog May 31, so please remember to check back!










