Cyber attacks are increasing. A continuous state of preparedness is required.
Cyber Security Compliance for Power, Oil & Gas, Water Treatment, NERC-CIP, NEI 0809 and CFATS
Thursday, March 28, 2013
Wednesday, March 27, 2013
Cyber Security: ICS-CERT Vulnerability Summary for Week of March 18
Click the link below to view the summary of cyber security vulnerabilities for the week of March 18 as collected and reported by ICS-CERT.
http://www.us-cert.gov/ncas/bulletins/SB13-084
http://www.us-cert.gov/ncas/bulletins/SB13-084
Cyber Security: Apple introduces two-factor authentication
Apple has introduced a long-needed security update for iTunes and iCloud users to prevent unauthorized charges to stored credit cards. Read about the new feature here.
Tuesday, March 26, 2013
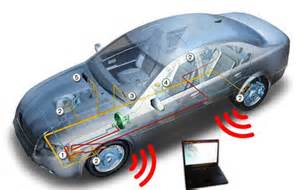
Cyber Security: Are cars the next cyber attack targets?
Cars could become a serious cyber attack target that could result in loss of life. Read how researchers were able to remotely manipulate a car, including shutting off the engine and locking all passenger doors, and what car audio and multimedia suppliers are saying about it.
Next cyber attack target: Cars?
Next cyber attack target: Cars?
Friday, March 22, 2013
Cyber Security: $33 million casino hack
One cyber criminal hacked his way into a casino's surveillance system and relayed information to a gambler through an earpiece, making millions. Read the article here.
Thursday, March 21, 2013
Cyber Security: ICS-CERT Vulnerability Summary for Week of March 11
Click the link below to view the summary of cyber security vulnerabilities for the week of March 11 as collected and reported by ICS-CERT.
http://www.us-cert.gov/ncas/bulletins/SB13-077
http://www.us-cert.gov/ncas/bulletins/SB13-077
Cyber Security: Celebrities hacked
Celebrities like Beyonce, Jay-Z, Paris Hilton, Kim Kardashian, Ashton Kutcher--even the First Lady, Vice President Biden, LAPD Chief, and the U.S. Attorney General--have all been recent victims of hacking and theft, whether it was personal information or thousands of dollars, sometimes both. Read the article here.
Wednesday, March 20, 2013
Cyber Security: Utilities likely to be victims of cyber attacks
California officials warn that increasing cyber attacks on utilities could leave millions without power and water, threatening the sick and elderly. Many utilities are becoming more and more vulnerable due to recent installations of smart meters and other technology. Read the article here.
Tuesday, March 19, 2013
Cyber Security: Hackers can cause traffic jams
German research suggests that hackers can manipulate traffic data and cause traffic jams, particularly through navigation software found in smartphones. Read the article here.
Thursday, March 14, 2013
Cyber Security: Apple's Macs become more targeted as popularity and sales increase
As Macs become more mainstream, they also become more targeted, as we saw last year with the Flashback Trojan. Kevin Haley, Symantec director of product management for security response, claims that Mac's biggest threat is third-party software like Adobe and Java and "drive-by downloads," where users only need to visit a website with a Java vulnerability to get infected.
http://www.siliconvalley.com/ci_22741463/apple-are-mac-computers-becoming-more-vulnerable-malware-virus?
http://www.siliconvalley.com/ci_22741463/apple-are-mac-computers-becoming-more-vulnerable-malware-virus?
Wednesday, March 13, 2013
Cyber Security: Obama to discuss strategies with CEOs to improve cyber security
Obama will meet with corporate leaders this afternoon to discuss strategies to improve cyber security and prevent more China-based cyber attacks. Even Michelle Obama may have been a victim of cyber crime, as Obama explained on ABC News that the White House is investigating whether her financial and personal information was posted online.
Last month, Obama gave an executive order to improve cyber security in an effort to safeguard the country's critical infrastructure.
Last month, Obama gave an executive order to improve cyber security in an effort to safeguard the country's critical infrastructure.
Cyber Security: ICS-CERT Vulnerability Summary for Week of March 4
Click the link below to view the summary of cyber security vulnerabilities for the week of March 4 as collected and reported by ICS-CERT.
http://www.us-cert.gov/ncas/bulletins/SB13-070
http://www.us-cert.gov/ncas/bulletins/SB13-070
Tuesday, March 12, 2013
Cyber Security: Organized crime hackers true threat to U.S. infrastructure
Earlier this month, a U.S. metropolitan utility suffered a massive DDoS attack that resulted in shutting down online and telephone payment services for 48 hours. The attackers responsible were not merely interested in causing mischief; rather, they were hardened criminals looking to make money by selling intellectual property and extorting their victims. Rentable crimeware and the ability to go undetected for months or years is bringing huge threats to American infrastructure with targeted cyber attacks, costing victims an estimated $110 billion a year, according to Symantec.
http://www.businessinsider.com/organized-crime-hackers-are-the-true-threat-to-american-infrastructure-2013-3
http://www.businessinsider.com/organized-crime-hackers-are-the-true-threat-to-american-infrastructure-2013-3
Thursday, March 7, 2013
Cyber Security: Online cloud storage an increasing security threat
As we saw with the recent breach of Evernote, the online storage firm, cloud-based storage has increased both in use and in risk as hackers begin targeting these types of websites and applications. Over a quarter of the world's business data is stored online, among other documents such as corporate, financial, and personal medical information.
http://www.insidebayarea.com/business/ci_22702191/cloud-use-grows-and-so-does-security-threat
http://www.insidebayarea.com/business/ci_22702191/cloud-use-grows-and-so-does-security-threat
Wednesday, March 6, 2013
Cyber Security Advisor Newsletter – Feb. 2013 Vol. 17
Welcome to the latest Global Cyber Advisor Newsletter,
There has been a lot of news lately of various government and extremist sponsored cyber-attacks. Large to small, companies, government agencies and private groups are targets of various attacks including information gathering for use at a later date. We need to stay vigilant and help our customers develop their Cyber Strategies and secure their process environments.
As we continue our efforts to educate on the need to address cyber security, the details that rise to the top are consistent. All successful Security Solutions are part of an overall program that addresses who will manage, maintain, and upgrade the solution for its lifetime. The latest and greatest technology can’t really just be dropped in and expected to perform, you must match it with your plans and strategy. The message is, consider what the needs are, develop a program, THEN determine the technical controls.
Cyber Security: Evernote online storage breached by hackers
Evernote, an online storage firm with over 50 million users, was hacked on February 28 and forced to reset passwords as a precautionary measure. Information such as usernames, email addresses, and passwords were accessed, but there was "'no evidence' that payment information or stored content had been accessed, changed or lost."
Evernote online storage breached by hackers
Evernote online storage breached by hackers
Tuesday, March 5, 2013
Cyber Security: Security Appliances
Gary Richardson, Invensys Critical Infrastructure & Security Practice consultant, explains how security appliances can fulfill multiple roles in defending networks.
In today’s cyber security landscape, a firewall is considered a paramount first line of defense in securing your networks. Many Distributed Control Systems, SCADA, Automation, and Process networks sit behind these devices that empower the nation’s critical infrastructure. While attacks on secure networks have increased in frequency and sophistication, firewalls have developed into security appliances capable of fulfilling multiple roles in defending networks. The current generation of security appliances offers the following technologies to enhance your cyber security solution:
Zone Segregation
Security appliances have the capability to segregate multiple networks into virtual zones within the device. This allows isolation of networks and the ability to control what flows in and out of the zones in great detail.
Rules and Policies
In addition to controlling traffic flows between zones, policies support the configuration of anti-virus, traffic inspection, logging, and specific ports and services to further define what is permissible data traversing your network.
Multi-Layer Operation
Security appliances have the capability of operating in a transparent mode or routed mode. In transparent mode, the device passes traffic at layer 2 and downstream nodes are unaware of the device. This allows the device to be implemented with a simple configuration and provides traffic logging and alerting. In routed mode, the device operates as a traditional firewall and router would, allowing segregation of network segments directly connected to the unit. Routing, NAT, or a combination of the two can be used to manage traffic paths.
Failover and Load Balancing
Most security appliances support high availability configurations. Traditionally, devices can be physically paired for stateful failover or configured independently for load balancing and failover purposes. To further enhance failover capabilities, monitors, triggers, and configuration integrity checks can be enabled.
Anti-Virus and Traffic Inspection
Security appliances possess the capability to inspect data streams for virus, Trojan, and worm signatures. Many appliances also feature traffic inspection at upper OSI layers as well as compressed data for attack signatures and behaviors. This feature allows the device to filter and alert on suspect traffic such as port scans, network mapping, and compressed payloads.
Logging and Alerting
While logging and alerting are certainly not new features, when paired with the aforementioned technologies they become an essential component of early detection and suppression of malicious
data in your environment.
Current generation security appliances have many features and technologies built into a single device. However, these devices should still be treated as point solutions and play an integral part of your overall cyber security program. A best practice layered approach should be a tiered, policy-based solution to ensure that the integrity of your cyber assets are protected and monitored.
Monday, March 4, 2013
Cyber Security: ICS-CERT Vulnerability Summary for Week of February 25
Click the link below to view the summary of cyber security vulnerabilities for the week of February 25 as collected and reported by ICS-CERT.
http://www.us-cert.gov/ncas/bulletins/SB13-063
Subscribe to:
Posts (Atom)